When good companies make catastrophic security decisions, it’s rarely by accident!
Why Good Companies Make Bad Security Decisions: The SolarWinds Wake-Up Call

The whole world nearly stood still, gob smacked by one of the most well coordinated cyberattacks in recent memory. SolarWinds, a trusted IT Company boasting 300,000 plus customers, including some of the biggest names in the public and private sector was under attack. A group of hackers, allegedly state-sponsored Russian operatives, had pulled off one of the most sophisticated cyber attacks of the new century, and in breaching SolarWinds; they had turned the company’s own software update system into a Trojan horse. The hackers inserted SUNBURST, a masterfully crafted piece of malware, into Orion’s legitimate update process. Like a poison pill wrapped in candy, this malicious code was automatically distributed to approximately 18,000 customers who simply followed standard security practices – keeping their systems up to date.

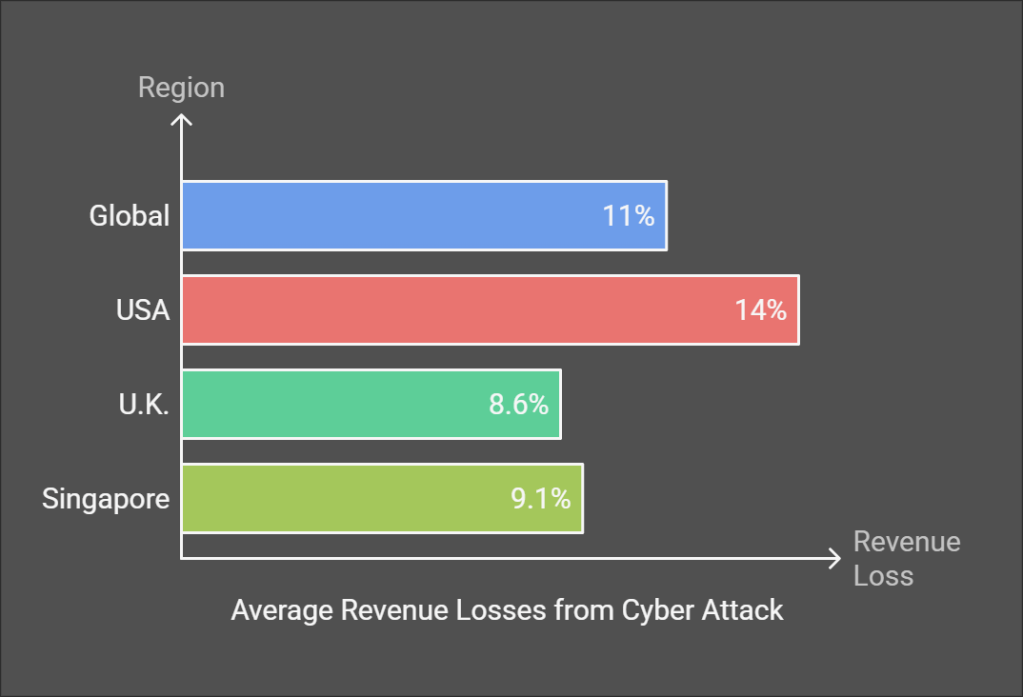
With a flamboyant client list including the US Department of Homeland Security, MasterCard, Subaru, Ernst and Young, New York times, this story grabbed the headlines and for good reasons. These industry titans reported the fallout from the attack. The financial hemorrhage that followed was staggering. Companies watched helplessly as the attack devoured, on average, 11% of their annual revenue – a number that tells only part of the story. American companies bore the heaviest burden, losing an average of 14% of their yearly earnings. Their counterparts across the pond fared slightly better, with U.K. businesses taking an 8.6% hit, while companies in Singapore grappled with losses of 9.1%. These weren’t just numbers on a spreadsheet; they represented shattered investor confidence, lost business opportunities, and millions spent on emergency security measures.
This incident marked a seismic shift in cybersecurity policy forever. In May 2021, President Biden issued an Executive Order on Cybersecurity, with specific provisions aimed at preventing another SolarWinds-style attack. The message was clear: in the modern digital ecosystem, even good security decisions (like regular updates) could lead to catastrophic outcomes.
Security Formation: How Companies Field Their Digital Defense
The SolarWinds breach demonstrated the high stakes of modern cybersecurity. But beyond these headline-grabbing disasters lies a more nuanced game—one that resembles not just any football match, but the strategic complexity of World Cup finals.

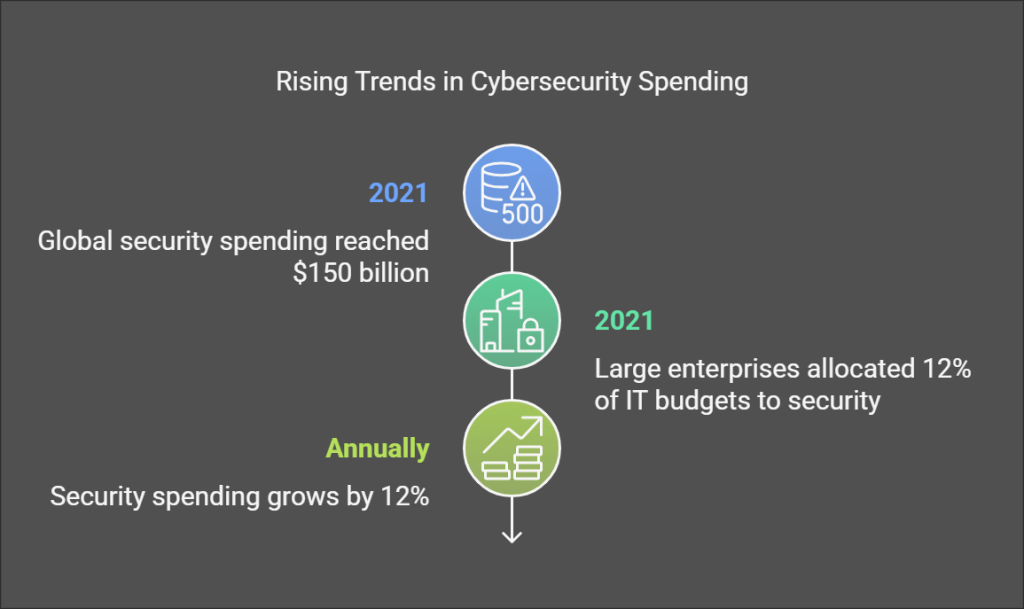
The difference between professional football teams and weekend warriors isn’t just skill—it’s strategy. Elite teams meticulously craft formations, analyze opponent tendencies, and develop sophisticated game plans. Similarly, enterprise cybersecurity only resembles amateur efforts on the surface. Where small businesses might implement basic security to “check a box,” Fortune 1000 companies invest significantly in security strategies tailored to their threat landscape. According to Gartner, global security spending reached $150 billion in 2021, with large enterprises allocating an average of 12% of their IT budgets to security—a figure that continues to grow by approximately 12% annually.
Regulations like GDPR function as the rulebook that shapes defensive structures. Just as Bayern Munich and Liverpool might both employ a 4-3-3 formation in the same match with dramatically different execution, companies within the same industry interpret regulatory frameworks distinctly.

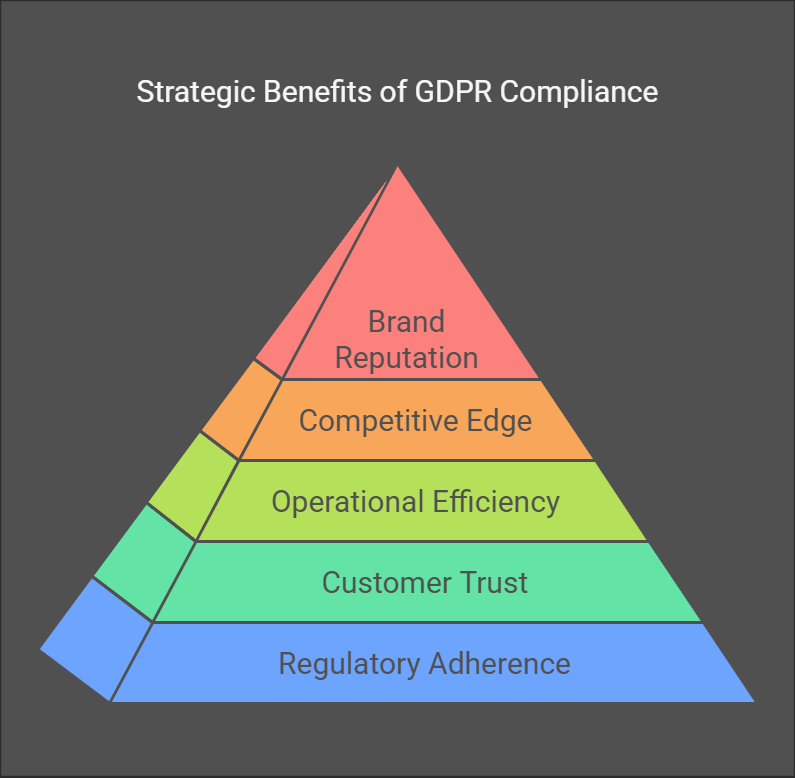
Achieving GDPR compliance not only ensures regulatory adherence but also offers strategic benefits, such as building customer trust, enhancing operational efficiency, and potentially gaining a competitive edge in the market. By prioritizing data privacy, businesses can differentiate themselves, reduce risks, and improve overall business continuity, ultimately leading to a stronger brand reputation and improved customer loyalty.
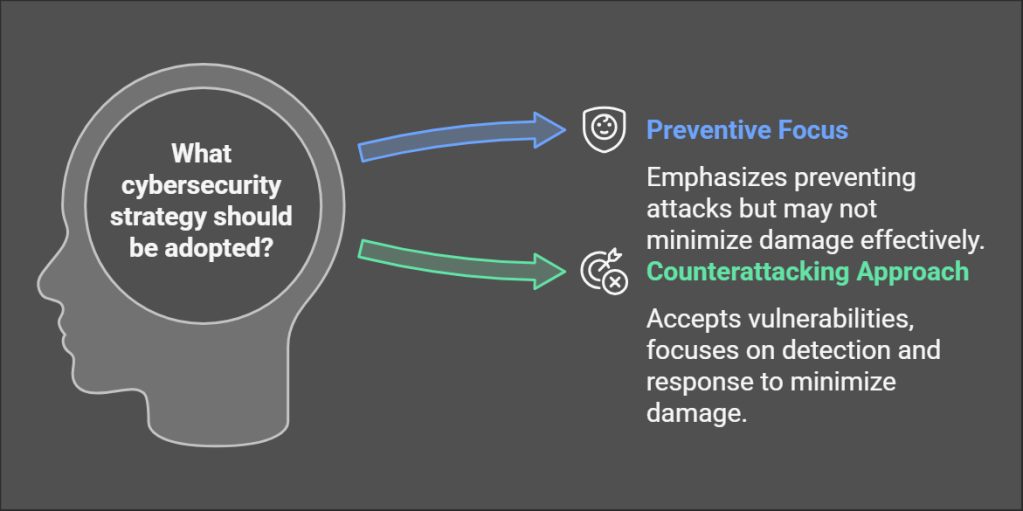
Some organizations employ the “decoy defense”—publicly highlighting certain security measures while quietly underinvesting in others. Like a soccer team showing a defensive setup before springing a surprise offensive press, these companies create security theater in visible areas while leaving critical vulnerabilities unaddressed. The 2020 Verizon Data Breach Investigations Report found that 43% of breaches involved web applications with security vulnerabilities that organizations had prioritized below more visible security initiatives.
Then there are the “counterattacking teams”—organizations that accept certain vulnerabilities but invest heavily in detection and response. According to IBM’s 2021 Cost of a Data Breach Report, companies with fully deployed security automation (including AI and machine learning) had an average total cost of a breach of $3.35 million, compared to $4.67 million at organizations with a less mature use of analytics, a difference of $1.32 million or 32.9% for those without such capabilities. These organizations, like defensive teams that absorb pressure before striking rapidly, focus on minimizing damage rather than preventing every attack.
The “possession-oriented teams” of cybersecurity are risk-averse organizations that prioritize control. High-risk industries worldwide, including healthcare and finance, prioritize tight control due to the sensitive nature of their operations and data. These sectors face significant challenges globally, such as frequent cyber incidents and substantial breach costs. Consequently, these industries invest heavily in advanced cybersecurity measures to safeguard sensitive data and ensure operational continuity. This proactive approach underscores their awareness of the severe global implications of cyber breaches, both financially and reputationally.
Perhaps most interestingly, the concept of “home field advantage” plays out dramatically in cybersecurity. Countries operating primarily within their local jurisdiction may enjoy several cybersecurity advantages. Local cybersecurity companies offer tailored solutions that are attuned to regional threat landscapes, providing a deeper understanding of local regulations and threats. This localized expertise enables rapid response times and compliance with specific regional standards, which can be particularly beneficial in highly regulated sectors like healthcare. Additionally, local operations often allow for better control over data management and infrastructure, potentially improving cybersecurity posture.
The SolarWinds attack revealed that even the most sophisticated teams can concede goals. But as in soccer, the difference between champions and relegation candidates isn’t whether they face attacks—it’s how well their defense is organized, how quickly they respond to unexpected threats, and how thoroughly they’ve prepared for the specific opponents they face.
Security Theater or Security Reality? When Companies Put on a Show
In the grand stadium of cybersecurity, many companies perform elaborate halftime shows—dazzling displays of security measures that impress stakeholders but leave critical vulnerabilities in their defensive line. This isn’t just metaphorical; it’s quantifiably real. According to IBM’s Cost of a Data Breach Report, the average breach cost reached a record $4.35 million in 2022, proving that despite impressive security performances, many organizations are conceding expensive goals.
Much like a football team that invests heavily in flashy attacking players while neglecting their defensive fundamentals, companies often prioritize visible security measures that satisfy compliance requirements without addressing foundational weaknesses. The Verizon Data Breach Investigations Report confirms this strategic error, revealing that a significant percentage of breaches still result from basic attacks like phishing and social engineering—the equivalent of repeatedly failing to defend against simple corner kicks that any well-drilled defense should handle routinely.
This disparity between security perception and reality resembles a team with beautiful uniforms and state-of-the-art facilities that consistently loses matches due to poor defensive coordination. Accenture research further validates this concern, showing that despite substantial investments in cybersecurity technologies, many organizations acknowledge their defensive formations remain vulnerable against increasingly sophisticated attack patterns. They’ve purchased expensive equipment but haven’t mastered the fundamentals of defensive positioning.

Consider how soccer teams approach defense—the best don’t merely react to attacks but anticipate them through careful study of opponent tendencies. Similarly, proactive security requires continuous monitoring and adaptation. Yet FireEye research indicates many organizations fail to implement this basic defensive strategy, leaving gaps for attackers to exploit—like a defender who never watches game film of opposing strikers.
The Championship Strategy: Building a Security Culture That Wins
For companies aiming to move beyond security theater and build genuine defensive resilience, here’s a championship-caliber approach:
- Train Your Entire Squad, Not Just Your Stars
The most successful football teams develop talent at every position, not just among star players. Similarly, research shows that organizations with security awareness programs experience 70% fewer security incidents which comes as no surprise considering that 82% of security breaches involve a human element. Invest in training across all departments, not just IT. - Practice Your Set Pieces
Championship teams rehearse defensive formations for specific situations. Implement regular tabletop exercises and simulated breach scenarios. According to Ponemon Institute, companies that regularly test their incident response plans reduce breach costs by an average of $2.66 million. - Scout Your Opponents
Elite teams study opponent tactics before matches. Implement threat intelligence programs to understand the specific threats targeting your industry. Mature threat intelligence programs improve an organization’s ability to detect and respond to threats more effectively. A survey conducted among 600 professionals showed that a mature threat intelligence program resulted in up to 51% faster breach response time. - Build Depth in Your Roster
The best teams boast incredible squad depth such that when key players are injured, these teams can turn to capable backups. Develop redundant security systems and make sure critical functions have failover capabilities. NIST guidelines emphasize this redundancy as essential for cyber resilience. The 3-2-1 strategy that involves maintaining 3 copies of data, one original and two backups is particularly genius - Develop a Winning Mindset
The best teams approach every match with discipline and focus, regardless of the opponent. Foster a security-first culture that treats even minor threats seriously. - Watch the replays
After matches, teams study what went wrong and right. Implement robust post-incident analysis procedures.
Just as in sports where champions win through smart plays rather than just big budgets, cybersecurity isn’t about spending more—it’s about executing well, following the rules, and building a strong, security-focused culture. Today’s companies need to meet legal requirements alongside their tech investments, turning these obligations into strategic strengths rather than burdens. By treating cybersecurity like a well-prepared sports team—with discipline, careful planning, and a keen eye on both strategy and legal compliance—organizations can move past mere show and create genuine defenses that hold up under pressure.
Happy Week!
Leave a comment